According to an impartial worldwide poll conducted by Cisco, employers and companies are skeptical about telecommuting technology and the efficacy of enterprises in safeguarding personal data as data on their safety, education, business, and social life are increasingly shared online.
What steps can businesses take to guarantee security?
To enable remote work, VPN for Windows and other free VPN providers, network equipment and devices, and networks may be updated with the latest security patches and configurations. 2+ Factor Authentication must be used for all VPN connections. If this is not possible, make it clear that remote employees use safe passwords. Training on the fundamentals of remote work should also be offered.
IT security personnel should evaluate VPN capability. To provide this chance to employees who want greater bandwidth, we must implement limitation rules.
All system-supported security processes must be correctly and thoroughly executed, produced tracking records (logs) must be regularly kept for future attack detection, and warning systems must be built for the detection of unauthorized entry, brute force assaults, and abnormalities.
What can users do to secure their remote work?
Systems used for remote work (PC, laptop, mobile, telephone, etc.) must also ensure that security software is activated, that software is up-to-date, and that there is no malware present.
Even while functioning remotely, critical data must not be retrieved or stored outside the company. It may be recommended that the systems in which non-critical data needs to be kept, duplicated, or delivered be monitored and that the confidentiality of such data is guaranteed.
1. Using iTOP VPN while working remotely:
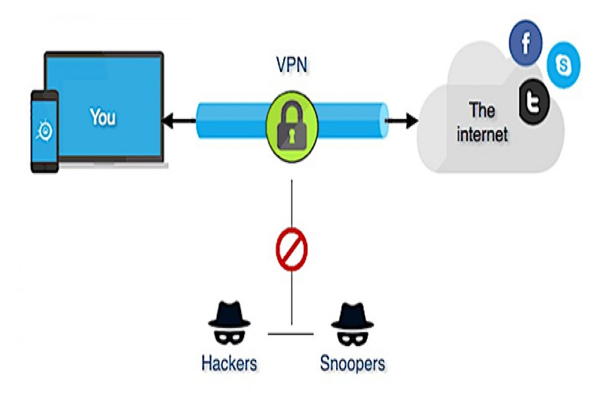
If business services must be networked remotely, be careful to configure a powerful VPN to provide a secure connection between computers and networks and protect corporate data from unwanted external access.
Additionally, you cannot access connections from external networks that route to the company network without a VPN. If your present employer does not supply a VPN infrastructure, you may easily resolve the issue on your own, since iTOP VPN software is simple to update and operate.
As a result of remote access, you may also exchange and transfer files, invite guests, and utilize other interactive communication tools. Remote access typically works by establishing a secure connection between a computer or mobile device and the network using particular protocols. Using a VPN- even a free VPN- to connect to a distant communication platform will encrypt your traffic and prevent cybercriminals from detecting or monitoring it.
2. Be wary of phishing attacks:
Before visiting domains that may include harmful software, such as websites and e-mails relating to the coronavirus, you should warn the IT and security staff and refrain from clicking on the relevant links.
You may also use Web and email filtering solutions for protection. Therefore, it is still simpler to identify spam emails, but since cyberattacks are now constructed in a highly sophisticated manner, you should not relax your vigilance.
3. Watch out for websites using the phrases COVID or Corona:
Hackers have started to register domains relating to coronavirus. Cybercriminals may purchase domain names (e.g., CDC-gov.org, cdcgov.org, etc.) that resemble trustworthy institutions such as the "World Health Organization" to entice users to click.
This does not imply that anybody who acquires a domain name with similar phrases is malevolent, but it might be difficult to determine if new domains launched on these terms constitute a lawful source of information. Users should thus not take secure access for granted.
No comments:
Post a Comment